North Korea’s new intercontinental weapon isn’t a missile. It’s a job application.
The Democratic People’s Republic of Korea (DPRK or North Korea) is capitalizing on the global demand for technical talent by flooding the market with “fake” workers—highly skilled North Korean nationals posing as US citizens.
I dug into this scam after reading about it in the Office of the Comptroller of the Currency’s (OCC) latest Semiannual Risk Perspective. The details are chilling. I hire for the exact roles the DPRK targets: remote, high-paying, and with access to data. In one recent interview I conducted, a candidate who was being considered had their camera off, a telltale sign of the scam. His responses were good, but now I’m wondering if he was looking up answers in real time, another tactic used by scammers.
Was I interviewing an operative? It’s hard to tell. The state-sponsored operation uses sophisticated technology to make the North Korean workers look like the candidates we want to hire. According to CrowdStrike’s 2025 Threat Hunting Report, DPRK-affiliated groups leverage generative artificial intelligence (GenAI) to help threat actors create attractive résumés and deepfake videos that mask the applicant’s true identity.
It’s easy to be duped. In fact, nearly every Fortune 500 company has hired a DPRK spy, Axios reported in August 2025. CrowdStrike investigated over 300 incidents in the last year alone. Even cybersecurity giants like KnowBe4 have fallen victim.
The Department of Justice (DOJ) has uncovered some of the plots. In December 2024, 14 North Korean state-sponsored scammers were indicted. In January 2025, the DOJ named 64 companies that had been victimized, including a U.S. financial institution.
But this is “just the tip of the iceberg,” says Special Agent in Charge Ashley T. Johnson of the FBI St. Louis Field Office.
Multiple Risks
The cybersecurity risks are obvious. DPRK IT workers use the privileged access gained as contractors or employees to facilitate malicious cyber intrusions, according to regulatory guidance issued in 2022. Some have even shipped U.S. company laptops home to Pyongyang, according to an FBI public service announcement.
Less obvious are the compliance risks posed by this scam. Banks that inadvertently hire a North Korean worker risk violating sanctions, as the salaries support the regime’s weapons of mass destruction (WMD) and ballistic missile programs. And when banks fail to detect the funds laundered to the regime, they risk violating the Bank Secrecy Act.[1]
Birthday Surprise
Not only are the tricksters good at getting hired, but they are also good at their jobs. After learning from Google Threat Intelligence that their firm had a North Korean on staff, a manager responded, “You guys better be right, because that is my best guy.” Another referred to their North Korean fraudster as “the most productive member of the team,” a CEO told Wired,
One company took a year to learn that it had hired a fraudulent programmer. The tip-off came at a video birthday celebration. ”It’s not my birthday,” he informed his colleagues. The pretender had apparently forgotten the birth date he entered into WorkDay.
An internal investigation revealed that the scammer was running a remote access tool on his work computer. The company let him go, but did not connect him to the North Korean IT worker scam. It was only later, when federal investigators discovered one of the birthday boy’s pay stubs at a North Korean laptop farm in Arizona, that the company realized it had employed a foreign agent for nearly a year, reported Wired.
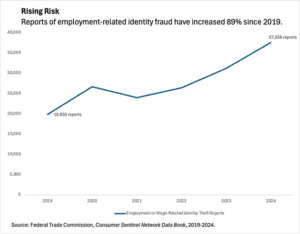
Rising Risk
While the scam has been around for years, it appears to be growing stronger. Employment-related fraud has increased by 89% since 2019 (see Figure 1).
Now, according to the OCC, the North Koreans are “targeting the financial sector.” Banks must update their hiring practices to thwart the threat. Even institutions that sidestep this scam could be criticized by regulators for not having controls in place to mitigate the risk.
Such controls need not be complicated. Start by educating human resources staff, hiring managers, and development teams about it. Because U.S.-based individuals are being recruited
[1] To launder the funds they receive, DPRK IT workers will request to be paid outside of the formal financial system in virtual currency, where Know your Customer (KYC)/Anti-Money Laundering (AML) measures are more easily evaded. Another red flag is frequent transfers of money through payment platforms, especially to People’s Republic of China (PRC)-based bank accounts, and sometimes routed through one or more companies to disguise the ultimate destination of the funds. See Guidance on the Democratic People’s Republic of Korea Information Technology Workers.
to apply on behalf of the DPRK, sloppy job applications could be a tell. Misspellings and odd addresses are often clues that the applicant is not who they claim to be. Alternatively, since the scam uses AI, a too-perfect resume could also be suspicious.
The right scrutiny during the interview can foil the fraud. Require that the applicant turn on their video and have an unobscured background. Notice unusual background noise. North Korean nationals engaged in this activity may be working against their will, and could be surrounded by other forced laborers. If you suspect something, ask your candidate to point the camera out a window.
Mandate in-person drug tests and/or fingerprinting to verify identity and claimed location. Verify their prior employment and education directly with the institution. In one case, the fraudster stole the identity of a dead U.S. citizen. This oversight could have been detected by speaking with someone who knows the person (or knew them).
If the interview seems otherwise normal, but you still sense something is off, ask the individual to wave their hand in front of their face. Motion can cause AI-generated video to malfunction.
On Guard
The benefit of remote work is undeniable. But this scam is increasing the costs. It’s easy to imagine all that could go wrong if a hostile power accessed our checking accounts—both business and personal. “The potential risk from even one minute of access to systems is almost unlimited,” Declan Cummings, the head of engineering at software firm Cinder, told Wired.
The OCC’s SARP has put financial institutions on guard. State-sponsored foreign adversaries want to infiltrate the U.S. financial system. It’s time to update our hiring practices and reduce the risk of hiring talent we may not ever meet in person. Especially when we put our most valuable resource—our data—in their virtual hands.
Figure 1 – Identity theft reports under the category “Employment or Wage-Related Identity Theft” include the use of a person’s identifying information to get a job, to get wages, and/or file taxes without their permission.
Cara Wick is a Global Financial Crimes Executive at Bank of America, Cara can be reached at [email protected].
[1] To launder the funds they receive, DPRK IT workers will request to be paid outside of the formal financial system in virtual currency, where Know your Customer (KYC)/Anti-Money Laundering (AML) measures are more easily evaded. Another red flag is frequent transfers of money through payment platforms, especially to People’s Republic of China (PRC)-based bank accounts, and sometimes routed through one or more companies to disguise the ultimate destination of the funds. See Guidance on the Democratic People’s Republic of Korea Information Technology Workers.